Python tool to Check running WebClient services on multiple targets based on @tifkin_ idea.
This tool uses impacket project.
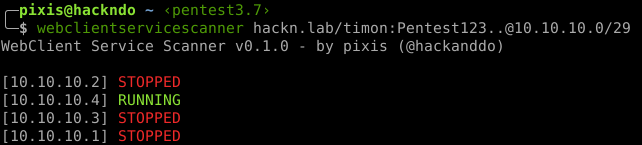
webclientservicescanner hackn.lab/user:S3cur3P4ssw0rd@10.10.10.0/24Provided credentials will be tested against a domain controller before scanning so that a typo in the domain/username/password won't lock out the account. If you want to bypass this check, just use -no-validation flag.
Green entries mean that WebDav client is active on remote host. Using PetitPotam or PrinterBug, an HTTP authentication can be coerced and relayed to LDAP(S) on domain controllers. This relay can use RBCD or KeyCredentialLink abuse to compromise relayed host.
For more info about relaying, you can check out https://en.hackndo.com/ntlm-relay/